5 Compelling Reasons to Read this Article (TEL/ETR: 13 min):
Q1. What is NIS2?
Q2. What is the significance and impact of NIS2 on organizations in Europe?
Q3. Is my organization required to comply with legal regulations by October 2024? ((See the summary table at the end for applicable industries and criteria))
Q4. Does compliance with this regulation involve high costs?
Q5. What are the best practices to optimize legal compliance at the lowest cost?
The NIS2 Directive complements standards like ISO27001, ISACA CSX, IT RISK 27005, PCI-DSS, DORA, GDPR, and Decree Law 65/2021.
Non-compliance with NIS2 places the responsibility for risks and damages directly on the organization’s management (Governance).
Q2: What is NIS2?
NIS2 (Network and Information Security Directive 2) is the updated version of the EU’s directive focused on improving cybersecurity and resilience of networks and information systems across the European Union. First adopted in 2016, the original NIS Directive marked the EU’s first significant cybersecurity legislation. However, the growing threat of cyberattacks and the evolving digital landscape necessitated updates and expansions in its provisions.
NIS2 introduces the following enhancements:
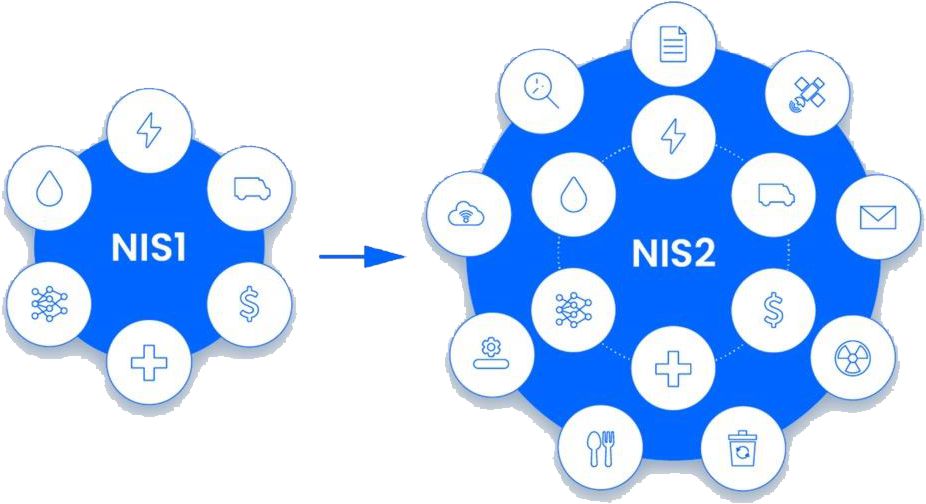
- Broader Scope: NIS2 now applies to additional sectors and types of entities, including critical areas like food, healthcare, energy, transport, water, telecommunications, digital services, waste management, and public administration.
- Strengthened Security Requirements: The directive enforces stricter security measures for organizations.
- Enhanced Cooperation: NIS2 fosters greater cooperation and information exchange between EU Member States and relevant authorities.
- Increased Oversight and Enforcement: National authorities will have more power to enforce NIS2 compliance, including the ability to impose sanctions for non-compliance.
NIS2 thus aims to create a more secure and resilient digital environment in the European Union, better protecting citizens and businesses against cyber threats.
ISO 27001 is an international standard that specifies the requirements for an information security management system (ISMS). It provides a framework for managing information security and ensuring that security controls are effectively implemented. Its connection to NIS2 lies in the fact that ISO 27001 can serve as a foundation for operators to meet the security requirements mandated by the directive.
The Cybersecurity Nexus (CSX) by ISACA is a certification and guidance framework for cybersecurity. While it is not a standard or legislation like NIS2, CSX offers resources and certifications that can help organizations build their cybersecurity capabilities, aligning with the compliance goals of NIS2.
ISO 27005 is a standard that provides guidelines for information security risk management. It complements ISO 27001 by offering a structured approach to identifying, assessing, and addressing risks. Risk management is a key component of NIS2, making ISO 27005 relevant for organizations seeking compliance.
The Payment Card Industry Data Security Standard (PCI-DSS) is a set of security standards designed to protect payment card information. While PCI-DSS is specific to the payments industry, the security principles it promotes are applicable to many of the security requirements of NIS2.
The Digital Operational Resilience Act (DORA) is another EU regulation focused on the digital operational resilience of financial entities. While NIS2 covers a broader range of sectors, DORA is specific to the financial sector, but both share the goal of strengthening cybersecurity resilience.
The General Data Protection Regulation (GDPR) focuses on the protection of personal data. While GDPR and NIS2 have different focuses, both require organizations to implement appropriate security measures to protect data and systems, creating an overlap in terms of security requirements.
Decree-Law 65/2021 is Portuguese legislation that transposes the original NIS directive into national law. It establishes security requirements for operators of essential services and digital service providers in Portugal. Its relationship with NIS2 is direct, as DL 65/2021 is the national implementation of the NIS directive, and it is expected to be updated to reflect the changes introduced by NIS2.
In summary, NIS2 is related to these standards, regulations, and frameworks through the common goal of enhancing cybersecurity and operational resilience, though each has its specific focus and scope.
Q2. What is the significance and impact of NIS2 on organizations in Europe?
The Importance and Impact of NIS2 on Organizations
NIS2 aims to improve the security of networks and information systems, minimizing the risks of cyberattacks and other threats. In today’s digital age, critical infrastructures and essential services increasingly rely on technology, making cybersecurity vital. The directive seeks to harmonize cybersecurity requirements across the European Union, ensuring that all Member States adopt a minimum level of protection. This uniformity promotes cross-border cooperation and coordinated responses to cybersecurity incidents.
Expanded Scope of Sectors
NIS2 covers additional critical sectors such as wastewater management, space, public administration, research, food production, chemical industries, postal services, and IT management (B2B). These sectors join existing ones like healthcare, energy, water, transport, and digital infrastructure, ensuring that essential services for society and the economy are better protected.
Organizations covered by NIS2 will have to comply with stricter cybersecurity requirements, which may involve additional investments in security technologies, staff training, and risk management processes.
National authorities will have more powers to oversee and audit the cybersecurity practices of organizations. This may lead to increased scrutiny and the need for companies to document and demonstrate their compliance.
NIS2 provides for the possibility of significant sanctions for organizations that fail to meet the established requirements. This increases the accountability of companies and could have a significant financial impact in case of non-compliance. For essential entities, fines can reach up to a maximum of €10 million or 2% of the organization’s total global annual turnover. For important entities, fines can go up to a maximum of €7 million or at least 1.4% of the organization’s total global annual turnover.
Organizations will be encouraged to cooperate more closely with national authorities and other stakeholders by sharing information about cybersecurity threats and incidents. This can improve incident response but will also require adjustments to internal communication and incident management processes.
The implementation of the measures required by NIS2 can increase organizations’ resilience against cyberattacks, protecting not only the organization itself but also its customers and partners.
NIS2 allows for compliance in 10 essential areas:
- Risk analysis policies and security of information systems (critical data and systems; information assets; secure access);
- Incident management (response time; damage containment; communication and channels);
- Business continuity (BCP), such as backup management (3-2-1-1) and disaster recovery (DRP), and crisis management (Article 21, paragraph 2, point c);
- Supply chain security (employees, suppliers, partners, and customers);
- Security of the acquisition, development, and maintenance of networks and information systems;
- Assessment of the effectiveness of cybersecurity risk management measures (regular tests and audits);
- Training in cyber hygiene and cybersecurity;
- Policies and procedures regarding the use of cryptography and, if applicable, encryption;
- Security of human resources, access control policies, and asset management;
- Use of multi-factor authentication solutions.
NIS2 represents an important step in strengthening cybersecurity in Europe but also imposes new challenges and responsibilities on organizations. Compliance with the directive will require a continuous commitment to improving security practices and adapting to new regulatory requirements, which will demand greater investment but with superior benefits.
Q3. Is my organization required to comply with any legal requirements (EU) by October 2024?
Yes, your organization may be required to comply with the NIS2 Directive by October 2024, depending on the sector in which it operates and the nature of its services. NIS2 introduces new cybersecurity requirements that apply to a broader range of sectors and types of entities compared to the original NIS Directive.
Sectors and Entities Covered
NIS2 covers a range of critical sectors, including but not limited to:
- Energy: Electricity, gas, oil.
- Transport: Air, rail, maritime, road.
- Banking: Financial institutions.
- Financial Market Infrastructures: Stock exchanges, clearing houses.
- Healthcare: Hospitals, clinics, pharmacies.
- Water and Waste: Water supply and waste management.
- Digital Infrastructures: Cloud service providers, data centers, content delivery networks.
- Public Services: Public administration, emergency services.
Compliance Requirements
Organizations covered by NIS2 will need to adopt cybersecurity measures, which may include:
- Risk Management: Implementation of policies and procedures to identify and manage cybersecurity risks.
- Technical and Organizational Measures: Adoption of security technologies and practices, such as firewalls, encryption, and staff training.
- Incident Reporting: Obligation to report significant cybersecurity incidents to the relevant authorities within specified deadlines.
- Audits and Supervision: Subject to audits and inspections by national authorities to verify compliance.
- Sanctions: Potential imposition of sanctions in case of non-compliance, including significant fines.
Steps to Take
- Compliance Assessment: Determine if your organization falls within the entities covered by NIS2.
- Gap Analysis: Conduct a gap analysis to identify areas where your organization does not meet NIS2 requirements.
- Action Plan: Develop an action plan to implement the necessary measures to achieve compliance.
- Training and Awareness: Invest in training and raising awareness among employees about the new cybersecurity requirements.
- Ongoing Monitoring: Establish continuous monitoring processes to ensure your organization maintains compliance over time.
If your organization operates in one of the mentioned critical sectors or provides essential services, it is urgent to start preparing for NIS2 compliance as soon as possible.
Note: Also see the summary table at the end of this article with industries and application criteria.
Q4. Does implementing this compliance have a high cost?
Implementing compliance with NIS2 can indeed entail significant costs for organizations, especially for those that need to make substantial changes to their cybersecurity practices. Here are some of the main factors that may contribute to the high costs:
- Technology and Infrastructure
- System Upgrades: Investment in security hardware and software, such as firewalls, intrusion detection and prevention systems, and encryption solutions.
- Network Infrastructure: Improvements to network infrastructure to ensure security and resilience against cyberattacks.
- Human Resources
- Hiring Specialists: Recruitment of qualified cybersecurity professionals, such as security analysts, security engineers, and risk managers.
- Training and Development: Continuous training programs for employees to ensure they are aware of cybersecurity best practices and NIS2 requirements.
- Processes and Policies
- Policy Development: Creation and implementation of cybersecurity policies and procedures aligned with NIS2 requirements.
- Risk Management: Establishment of robust risk management processes, including regular risk assessments and security audits.
- Monitoring and Incident Response
- Monitoring Systems: Implementation of continuous monitoring systems to detect and respond rapidly to cybersecurity incidents.
- Incident Response Plans: Development and testing of incident response plans to ensure effective responses in case of a cyberattack.
- Consulting and Auditing
- Consulting Services: Hiring specialized consultants to assist with compliance assessment and implementation of necessary measures.
- Compliance Audits: Conducting internal and external audits to verify compliance with NIS2 and identify areas for improvement.
Long-Term Benefits
Although the initial implementation costs may be high, it is important to consider the long-term benefits:
- Reduction in Cyberattack Risk: Implementing robust cybersecurity measures significantly reduces the risk of cyberattacks and potential financial losses associated with them.
- Reputation and Trust: Demonstrating compliance with NIS2 enhances trust among customers, partners, and other stakeholders in your organization.
- Operational Efficiency: Improving the security of networks and information systems leads to greater operational efficiency and reduces disruptions caused by cybersecurity incidents.
While the implementation of NIS2 compliance can represent a significant investment, these costs should be viewed as a necessary measure to protect the organization against cyber threats and ensure the continuity of essential services. A proactive and well-planned approach can help mitigate costs and maximize long-term benefits.
On the other hand, the decision not to invest in digital security means accepting the inherent risks, including losing all data and customer information or allowing external entities (hackers, terrorists, etc.) access to your customer’s data, violating contracts or data protection laws, which could lead to the ruin and closure of your business.
Q5. What are the best practices for optimizing legal compliance at the lowest cost?
Compliance with NIS2 can be optimized at the lowest cost through the adoption of various best practices. Here are some strategies that can help reduce costs while maintaining a high level of cybersecurity:
- Risk Assessment and Planning
- Initial Risk Assessment: Conduct a detailed risk assessment to identify the most vulnerable and priority areas. Focusing resources on high-risk areas can prevent unnecessary spending.
- Strategic Planning: Develop a phased implementation plan to spread costs over time. Prioritize the most critical and impactful actions.
- Utilizing Internal Resources
- Leverage Internal Talent: Identify employees with cybersecurity skills and provide internal training. This can reduce the need for hiring new specialists.
- Cross-Training: Encourage cross-training between departments to increase resilience and incident response capability.
- Automation and Open Source Tools (BPM; HyperAutomation) with Open Source Tools (Java, Linux)
- Process Automation: Use automation tools such as BPM (automated workflows) or HyperAutomation (with AI) for monitoring, threat detection, and incident response. This can reduce manual workload and improve efficiency.
- Open Source Tools: Utilize open-source cybersecurity solutions, which are often free or low-cost, to complement some of your defenses.
- Managed Security Services
- Outsourcing Services: Consider outsourcing some cybersecurity functions to Managed Security Service Providers (MSSPs). This can be more cost-effective than maintaining an internal dedicated team.
- Strategic Partnerships: Establish partnerships with other organizations to share knowledge, resources, and cybersecurity-related costs.
- Effective Policies and Procedures
- Clear and Concise Policies: Develop clear and simple cybersecurity policies that are easy to follow and implement, tailored to the size and reality of your organization.
- Incident Response Procedures: Create clear and well-documented incident response procedures, including defining roles and responsibilities, to ensure a swift and effective response.
- Training and Awareness
- Awareness Programs: Invest in awareness and continuous training programs for all employees. Training can prevent many cybersecurity incidents caused by human error—about 82% of incidents have an internal human origin (Verizon DBIR, 2022).
- Simulations and Testing: Conduct cyberattack simulations and incident response tests to prepare the team and identify areas for improvement.
- Continuous Monitoring and Review
- Continuous Monitoring: Establish ongoing monitoring and review processes for cybersecurity measures to ensure they remain effective and aligned with evolving threats and requirements.
- Internal Audits: Perform regular internal audits to ensure compliance and identify areas where improvements or savings can be made.
- Utilizing Grants and Incentives
- Government Support: Investigate the availability of grants, tax incentives, or other government support for cybersecurity initiatives.
- EU Programs: Explore programs and funds available from the EU.
Optimizing NIS2 compliance at the lowest cost requires a strategic and well-planned approach. By focusing on high-risk areas, leveraging internal resources, using cost-effective tools, and establishing partnerships, your organization can achieve a high level of cybersecurity without incurring excessive costs.
We have a senior and certified team to assist your organization with compliance assessment and scope (NIS2, ISO27k1, RGPD, Law 65/2021), security risk analysis, information security plan development, implementation program management, or professional services and CISOaaS.

by Jorge Pereira – Co-Founder &CEO @Uniksystem
Partilhe!

